搭建 Kubernetes 镜像私服
Mr.Lee 2025-05-09 22:29:23 Kubernetes
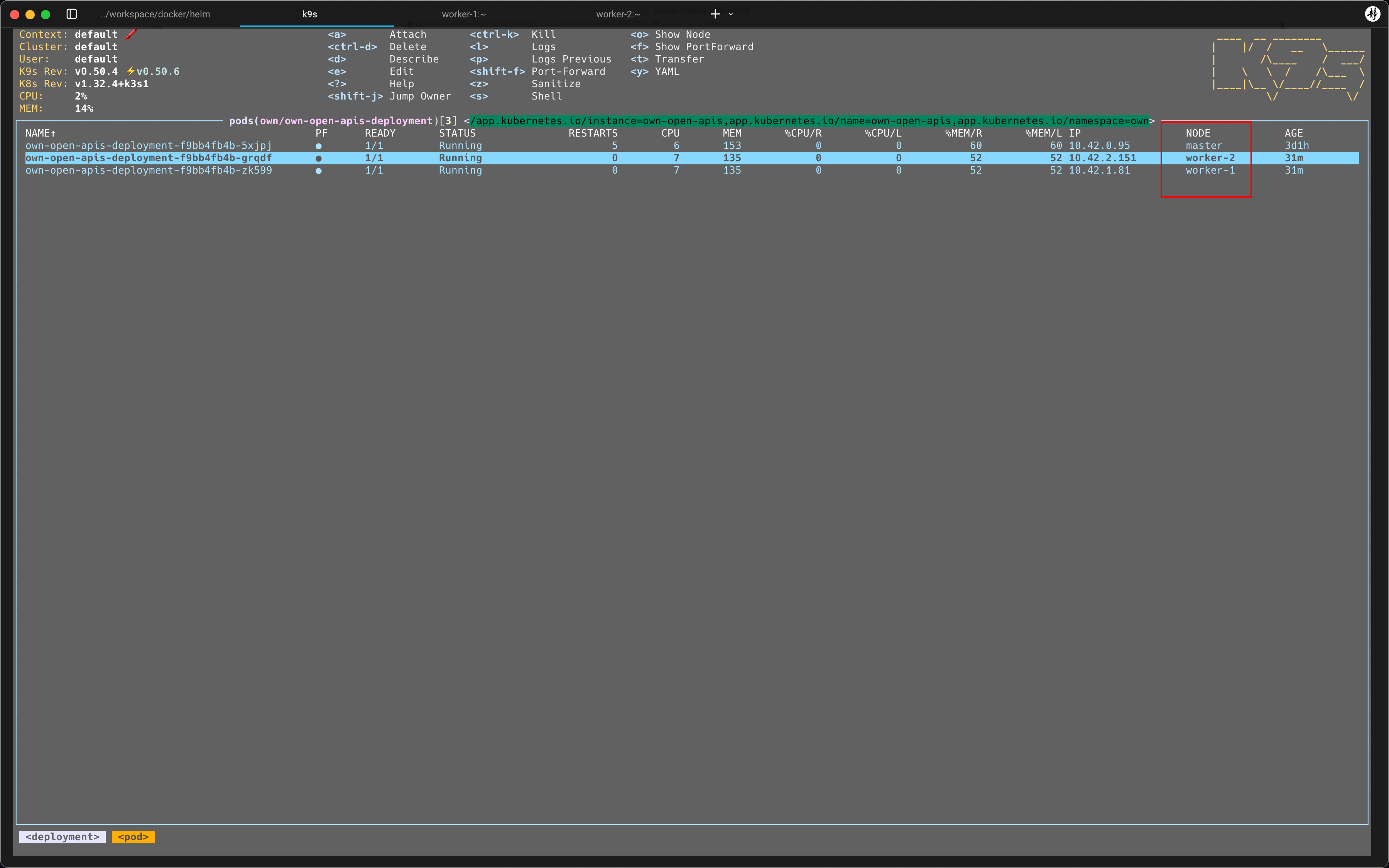
书接上回, 上次咱们将 own-open-apis 项目, 部署到了 Kubernetes 集群环境中. worker-* 节点拉取镜像还会有问题...今天我们就来尝试解决一下这个问题
闲言少叙, 开始正文
我的思路是在宿主机上装个 Harbor 完事了呗, 这样我想在集群环境中部署应用时, 就不用在往里面拷镜像了, 只需要同步 Chart 包就可以了.
来, 看一下开始的效果是这样的 [捂脸]
# 安装私服
# 1.下载helm-chart安装包
❯ helm pull oci://registry-1.docker.io/bitnamicharts/harbor --version 24.0.1
Pulled: registry-1.docker.io/bitnamicharts/harbor:24.0.1
Digest: sha256:f5622b24a26bf521d19b451e6f179603542658f509d3e3f01451af018ea2385f
# 2. 安装 Harbor
❯ helm install harbor harbor-24.0.1.tgz --namespace infrastructure --create-namespace \
--set exposureType=ingress \
--set ingress.core.tls=true \
--set ingress.core.selfSigned=true \
--set adminPassword=ePKfDkBHhfbhwH0JUxY2e8
NAME: harbor
LAST DEPLOYED: Mon May 12 16:33:42 2025
NAMESPACE: infrastructure
STATUS: deployed
REVISION: 1
TEST SUITE: None
NOTES:
CHART NAME: harbor
CHART VERSION: 24.0.1
APP VERSION: 2.11.1
** Please be patient while the chart is being deployed **
1. Get the Harbor URL:
You should be able to access your new Harbor installation through https://core.harbor.domain
2. Login with the following credentials to see your Harbor application
echo Username: "admin"
echo Password: $(kubectl get secret --namespace infrastructure harbor-core-envvars -o jsonpath="{.data.HARBOR_ADMIN_PASSWORD}" | base64 -d)
WARNING: There are "resources" sections in the chart not set. Using "resourcesPreset" is not recommended for production. For production installations, please set the following values according to your workload needs:
- core.resources
- exporter.resources
- jobservice.resources
- nginx.resources
- portal.resources
- registry.controller.resources
- registry.server.resources
- trivy.resources
+info https://kubernetes.io/docs/concepts/configuration/manage-resources-containers/
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
注意: 这是在宿主机上哦~
修改 hosts 文件
❯ echo "127.0.0.1 core.harbor.domain" | sudo tee -a /etc/hosts
❯ source ~/.zshrc
❯ ping core.harbor.domain -c 1
PING core.harbor.domain (127.0.0.1): 56 data bytes
64 bytes from 127.0.0.1: icmp_seq=0 ttl=64 time=0.040 ms
--- core.harbor.domain ping statistics ---
1 packets transmitted, 1 packets received, 0.0% packet loss
round-trip min/avg/max/stddev = 0.040/0.040/0.040/0.000 ms
1
2
3
4
5
6
7
8
9
10
11
2
3
4
5
6
7
8
9
10
11
打开地址: https://core.harbor.domain/harbor/projects
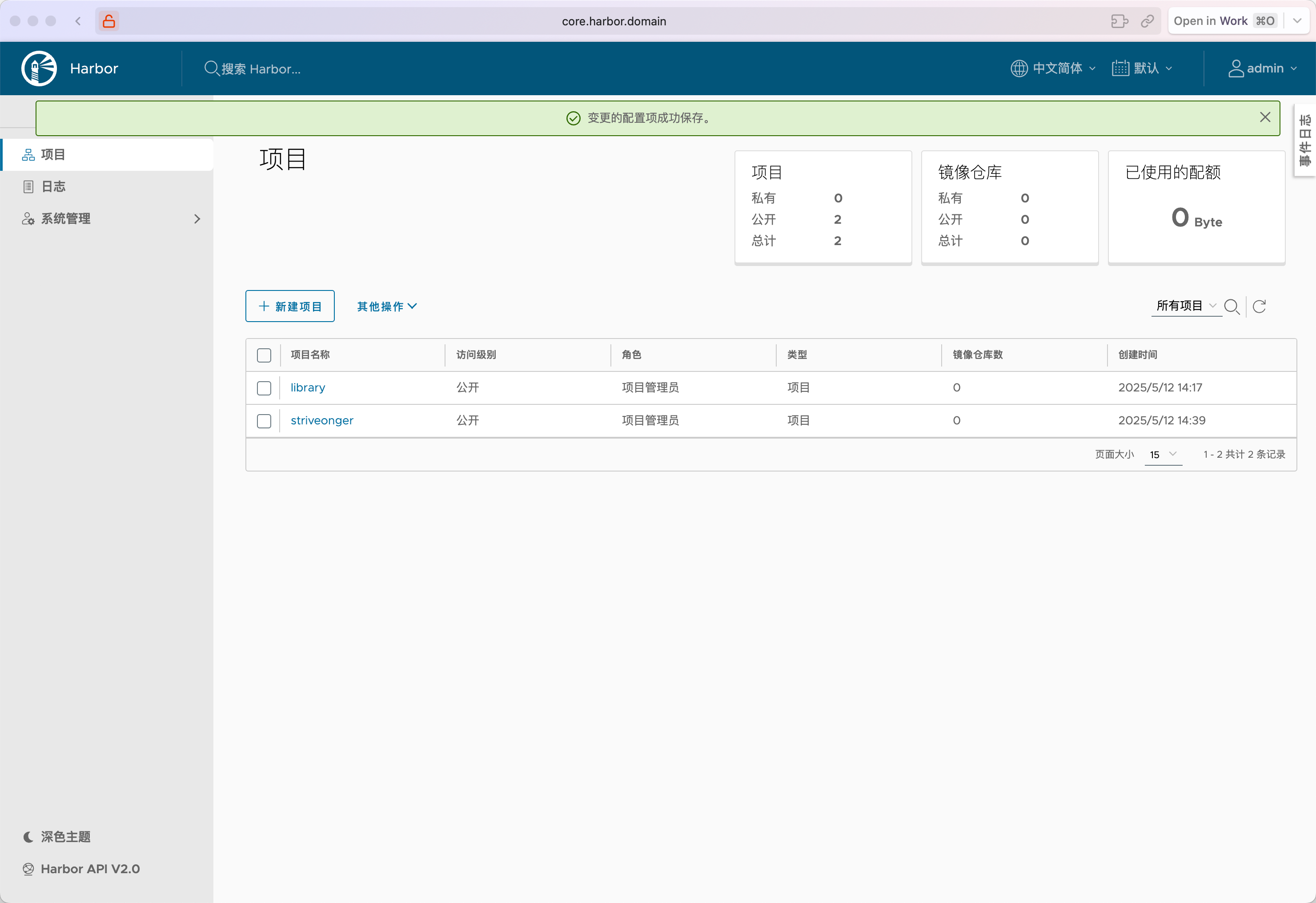
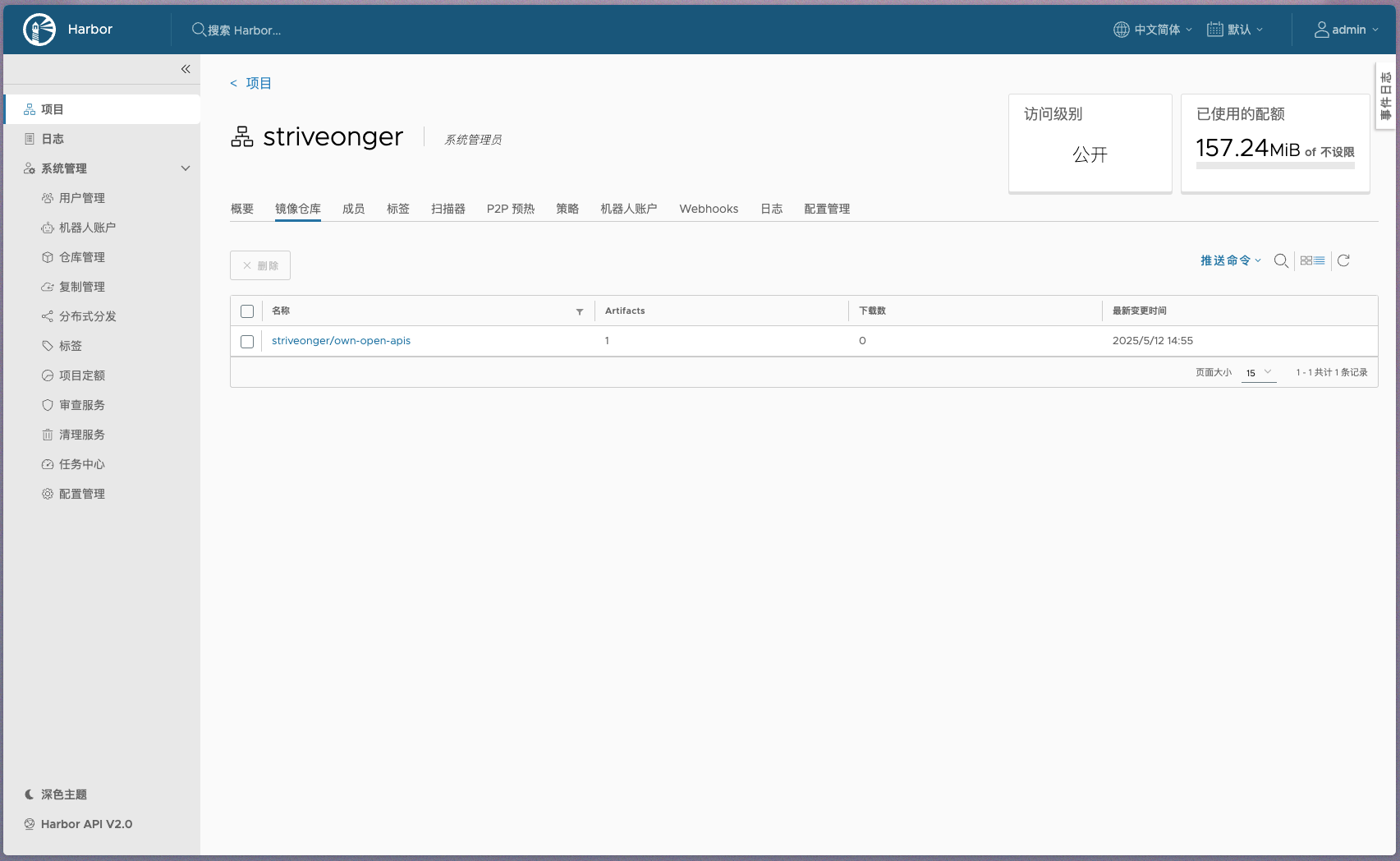
新建了个项目, 并改为公开
# 推送镜像
# 重新打包
❯ docker tag striveonger/own-open-apis:1.0.0 core.harbor.domain/striveonger/own-open-apis:1.0.0
# 登录(反正是本地使用, 密码明文也无所谓了....)
❯ docker login core.harbor.domain -u admin -p ePKfDkBHhfbhwH0JUxY2e8
WARNING! Using --password via the CLI is insecure. Use --password-stdin.
Login Succeeded
# 向私服推送镜像
❯ docker push core.harbor.domain/striveonger/own-open-apis:1.0.0
The push refers to repository [core.harbor.domain/striveonger/own-open-apis]
db5dd49de3f2: Pushed
cff61dad21a4: Pushed
d84b4d03bebc: Pushed
a6018fb8972b: Pushed
5e97e47c11c1: Pushed
3aba462813f2: Pushed
de085928b8c4: Pushed
1.0.0: digest: sha256:a8abb93724c26480e59329ef6d6e148c317ff532ad38e58cae18a5c4ba7a7674 size: 1786
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
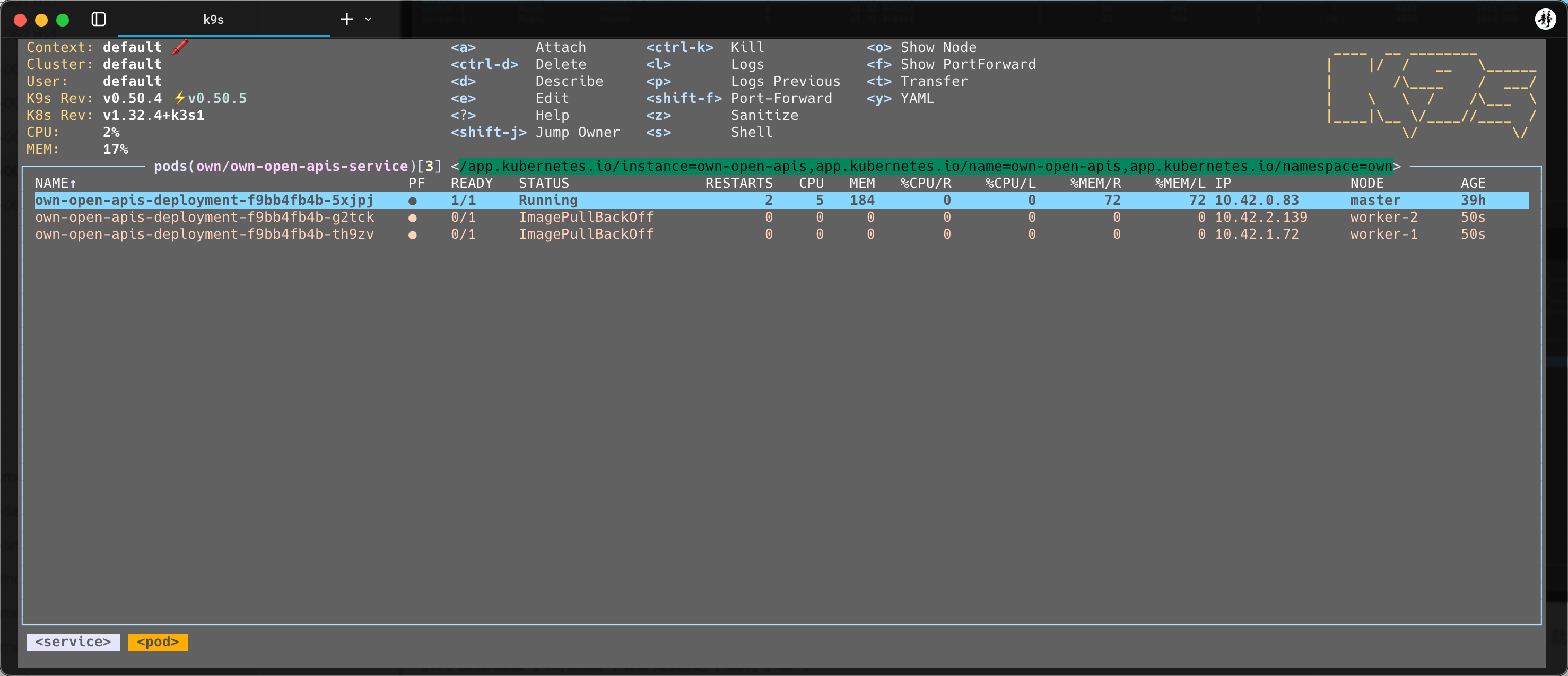
推送成功~
# 配置私服
在集群环境中配置镜像私服
# 三台虚拟机都要执行
# 1. 配置域名
❯ echo "10.13.147.1 core.harbor.domain" | sudo tee -a /etc/hosts
# 2. 测试是否配置成功
❯ ping core.harbor.domain -c 1
PING core.harbor.domain (10.13.147.1) 56(84) bytes of data.
64 bytes from core.harbor.domain (10.13.147.1): icmp_seq=1 ttl=64 time=0.189 ms
--- core.harbor.domain ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 0.189/0.189/0.189/0.000 ms
# 3. 修改前
❯ cat /etc/rancher/k3s/registries.yaml
mirrors:
"docker.io":
endpoint:
- "https://registry.cn-hangzhou.aliyuncs.com"
"k8s.gcr.io":
endpoint:
- "https://registry.cn-hangzhou.aliyuncs.com/google_containers"
"quay.io":
endpoint:
- "https://quay.mirrors.ustc.edu.cn"
# 4. 修改文件内容
❯ sed -i '/"docker.io":/,/endpoint:/ {
/endpoint:/ {
n
i\ - "https://core.harbor.domain"
}
}' /etc/rancher/k3s/registries.yaml
# 5. 修改后
❯ cat /etc/rancher/k3s/registries.yaml
mirrors:
"docker.io":
endpoint:
- "https://core.harbor.domain"
- "https://registry.cn-hangzhou.aliyuncs.com"
"k8s.gcr.io":
endpoint:
- "https://registry.cn-hangzhou.aliyuncs.com/google_containers"
"quay.io":
endpoint:
- "https://quay.mirrors.ustc.edu.cn"
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
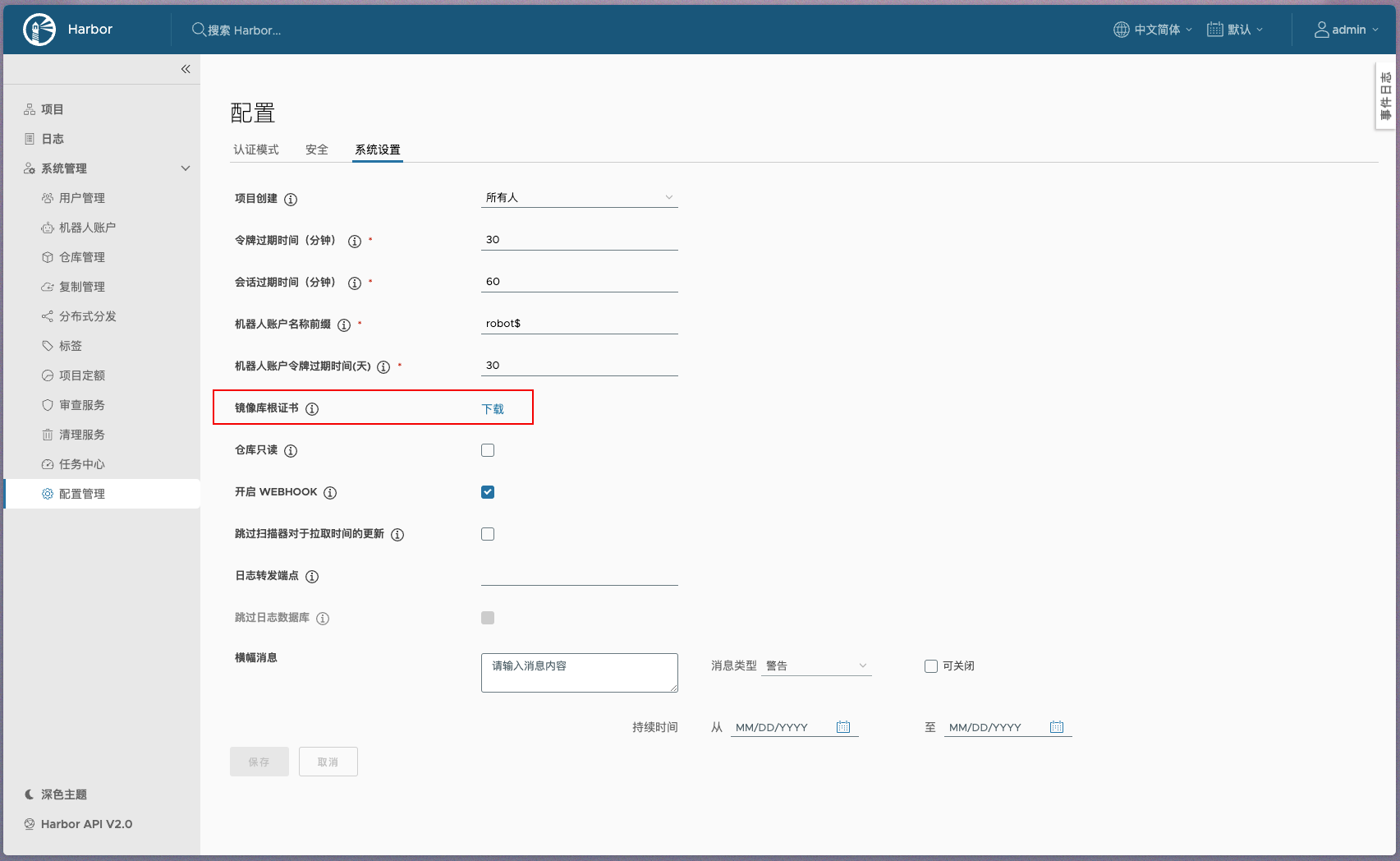
# 配置TLS证书
下载证书
# 宿主机 SCP
❯ scp ./harbor-ca.crt root@10.13.147.9:/root
harbor-ca.crt 100% 1127 1.9MB/s 00:00
❯ scp ./harbor-ca.crt root@10.13.147.10:/root
harbor-ca.crt 100% 1127 2.4MB/s 00:00
❯ scp ./harbor-ca.crt root@10.13.147.11:/root
harbor-ca.crt 100% 1127 2.4MB/s 00:00
# 虚拟机添加信任证书 (三台机器)
❯ cp harbor-ca.crt /usr/local/share/ca-certificates/
❯ ll /usr/local/share/ca-certificates/
total 4.0K
-rw-r--r-- 1 root root 1.2K May 12 16:58 harbor-ca.crt
❯ sudo update-ca-certificates
Updating certificates in /etc/ssl/certs...
rehash: warning: skipping ca-certificates.crt,it does not contain exactly one certificate or CRL
1 added, 0 removed; done.
Running hooks in /etc/ca-certificates/update.d...
done.
# Containerd添加信任证书
❯ sudo mkdir -p /etc/containerd/certs.d/core.harbor.domain
❯ cp harbor-ca.crt /etc/containerd/certs.d/core.harbor.domain/ca.crt
❯ ll /etc/containerd/certs.d/core.harbor.domain/
total 4.0K
-rw-r--r-- 1 root root 1.2K May 12 17:05 ca.crt
❯ sudo systemctl restart containerd
# 若使用K3s,重启K3s服务
❯ sudo systemctl restart k3s
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
# 成果展示